Good questions.
- Is my AD account now the account which is used by the instance?
This depends on the setting that you choose in the data connector

Server Windows Credentials - Uses the account that you used as a service account when you installed Dundas BI. This is typically something like NETWORK_SERVICE but you can change it in the application config.
User SQL Server Authentication - Allows you to specify an account that the data connector will always use for everyone.
Specified Windows Credentials - This option will be the one you use if you want the data connector to always use your AD account or a specific one that you enter. Usually you would use this option if you were hoping to have data returned using a specific service account.
Impersonated Windows Credentials - This options changes the account used to access the Database based on the user accessing the content.
For example:
User A logs into Dundas BI (using their AD account). If they use this data connector, the data connector uses DOMAIN\usersA
User B logs into Dundas BI (using their AD account). If they use this data connector, the data connector uses DOMAIN\usersB
Active Directory Password - Similar to Specified Windows Credentials but for SQL Azure
Active Directory Integrated - Similar to Server Windows Credentials but for SQL Azure
-
I think i may have answered this in my long explanation above. Instead of using the db.config, use a different data connector option.
-
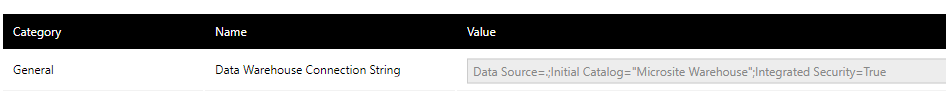
This is an option being fed directly into the connection string. I assume for this question that you are talking about the Dundas BI config and not the data connector. This setting is used within the data connector but it’s abstracted for you by using the options described in #1 above.
Integrated Security = False : User ID and Password are specified in the connection.
Integrated Security = True : the current Windows account credentials are used for authentication